

A hospitality company was awarded a $50 Best Buy gift card in a letter that also included a USB t...
Baptist Health Medical Group operates and relies on an extensive system of medical devices, IoT, ...
Baptist Health is a full-spectrum health system made up of nine hospitals, 23,000 employees (in a...
A highly targeted government entity shuts its doors to unauthorized hardware devices. A top-notch...
Cyber Crime organizations and state sponsored groups use manipulated hardware or firmware, deli...
Following an investigation by a cybersecurity firm, it was found that the USB device was the sour...
In 2019, a Chinese woman, Yujing Zhang, entered President Trump’s Mar-a-Lago resort claiming she...
Complete and accurate visibility into network and peripheral devices.
As part of an academic security research that included the scanning of repositories of files, r...
A Tier 1 bank audit revealed some irregularities and it became evident that an external party ha...
Sepio Systems is the leader in Visibility, Control and Mitigation of hardware assets and is disr...
A report on the cybersecurity risks of M&A by Forescout showed that 62% of organizations agree ...
Enterprises are challenged with gaining accurate visibility into hardware assets, especially in ...
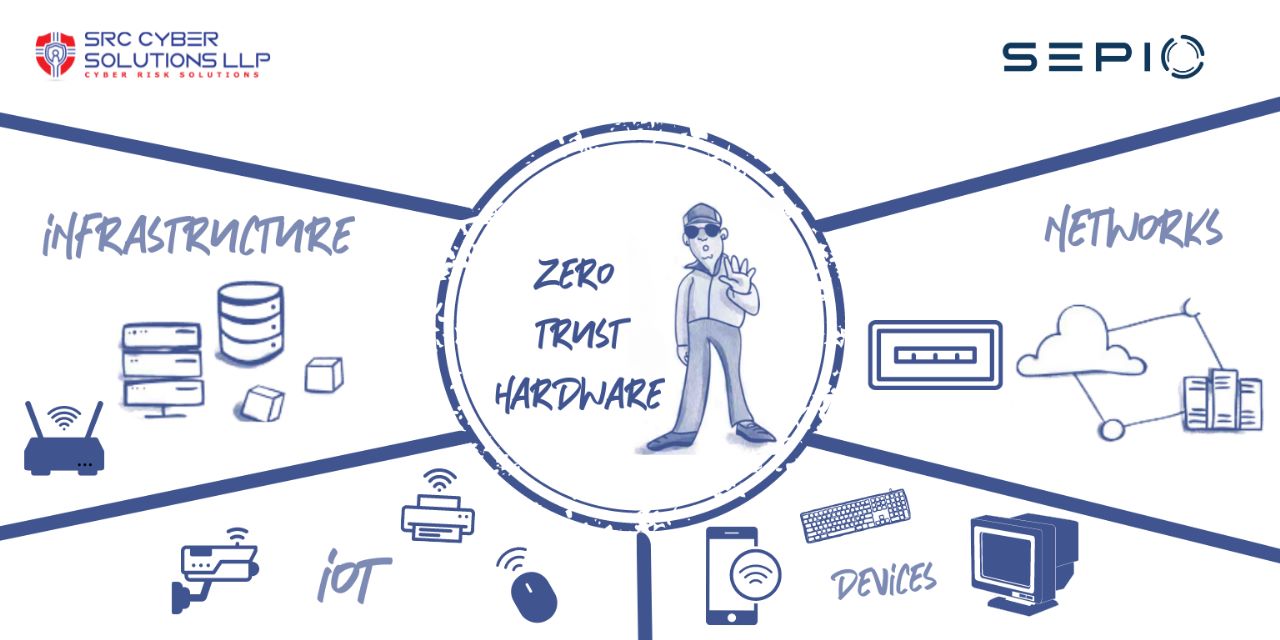
Zero Trust is a network security model based on the principle of “never trust, always verify”. B...
The new Cybersecurity Maturity Model Certification is the US Department of Defense’s response to...
Today’s world and economies are highly interconnected. With this interconnection, supply chains...
Automated teller machines (ATMs) are a prime target for cybercriminals. Some ATMs are filled wi...
ATM usage is undeniable, with the average ATM being used 300 times a month, and over 10 billion ...
Bring Your Own Device (BYOD) is a trend whereby employee-owned devices are being used within a ...
Critical infrastructure is recognised by governments as the body of systems, networks and assets...
Data centers are facilities that centralize an organization’s shared IT operations and equipment...
The healthcare industry is a vital component of a nation’s critical infrastructure. The various ...
Organizations also need to be aware of insiders who purposefully reveal confidential and sensiti...
Today, Wi-Fi is everywhere; we find it in homes, offices, coffee shops, airports, hospitals, and...
The number of organizations that are using MSSPs has increased over the years for various reaso...
Section 889 is part of the National Defense Authorization Act (NDAA) for Fiscal Year 2019. The ...
The pharmaceutical industry is one of the most vital industries in the world; discovering, devel...
PoisonTap is built for Raspberry Pi and produces a cascading effect by exploiting the existing t...
Supply chain threats are present during the various phases of an information system’s developme...
Operational technology (OT) is the hardware and software responsible for physical processes, devi...
model but also a mindset. ZT is based on the idea that threat exists everywhere, both inside and...
3 Challenges CISOs face managing risk postures
Watch NowHow do you manage the intricacies of regulation
Watch NowHow do you tackle gaining asset visibility in complex infrastructure
Watch NowHow will the landscape for global financial institutions change in terms of emerging risk
Watch NowNo E-books available.
1.png)
30-Oct-2023
One of the common use cases raised by Sepio’s customers is for those who operate in highly regula...

30-Jan-2024
In the world of network security, government entities face unique challenges when it comes to saf...

28-Sep-2023
Feel like you're drowning in a tsunami of hardware components?

28-Jun-2022
IoMT Devices Have a Higher Risk Posture Hospitals around the globe have realized that proper cyb...

28-Feb-2023
The process of identifying what may be connected to your network, known and unknown, fits perfect...

28-Feb-2023
This most recent revolution involves the application of IT technology to industry; in short, it i...

28-Feb-2023
Installing Sepio’s Hardware Access Control (HAC-1) solution, the first of its kind, was truly eye...

28-Feb-2023
Sepio’s Hardware Access Control (HAC-1) solution provides a panacea to gaps in device visibility ...

28-Feb-2023
HAC-1’s policy enforcement mechanism and Rogue Device Mitigation capabilities instantly block any...

28-Feb-2023
As described in the Department of Defense Zero Trust Reference Architecture, “The foundational te...

28-Feb-2023
Here at Sepio we like to stress the importance of Layer 1 visibility. But why is Layer 1 in the O...

28-Feb-2023
Sepio’s technology enables data protection at an unprecedented level thanks to complete device vi...
28-Feb-2023
Connected assets in financial institutions are growing at a rapid pace. Having an efficient and a...

28-Feb-2023
Connected assets in medical facilities are growing at a rapid pace. To have full control of your ...

28-Feb-2023
Sepio’s HAC-1 is the only Hardware Access Control solution that provides Layer 1 visibility, cont...

28-Feb-2023
Shadow IT refers to information systems deployed by departments other than the central IT departm...
28-Feb-2023
Hardware assets are all around us and in growing numbers – which indicates what an impossible tas...

28-Feb-2023
Need a solution that will help you monitor and keep track of all your hardware assets?

28-Aug-2023
IT asset management (ITAM) and configuration management database (CMDB) are two platforms that s...

27-Feb-2023
Airports are part of a nation’s critical infrastructure. As such, they are constant targets for c...

27-Feb-2023
Modern vehicles rely on computers for all their core functions. Modern vehicles are equipped with...

26-Dec-2023
In today’s dynamic cybersecurity landscape CISOs know that traditional NAC solutions which were s...

25-Oct-2023
A Sepio customer, who deployed a NAC solution, implemented a MAC based security policy. When chal...

24-Jul-2023
Data centers are facilities that centralize an organization’s shared IT operations and equipment,...

24-Feb-2023
IoT devices also provide advantages in the workplace. As a result, these devices are increasing i...

24-Apr-2023
Cybersecurity is no longer just a matter of securing the perimeter of an organization’s network. ...

23-Aug-2022
Cyber Security in the Financial Sector Needs Asset Visibility Financial institutions are faced w...

22-Mar-2023
Darknet Diaries, for the few who aren’t already avid listeners, combines stories from the dark si...
21-Apr-2021
Embracing a Zero Trust Hardware Access Security Model is key.

17-Oct-2023
As the digital landscape expands, organizations are confronted with an ever-increasing array of c...

17-May-2022
The First Industrial Revolution began in the 18th century. Today, as technology evolves even more...

17-Jul-2023
The integration of IT, OT, and IoT domains has transformed traditional tools like laptops and sma...

17-Jan-2024
A Timely Directive from The White House, regarding the Internet of Things (IoT) inventory managem...

15-Mar-2023
You are a security specialist for a large bank – if asked, most would categorize your organizatio...

13-Jun-2023
You wouldn’t want to hear that the supplier that provides your local supermarket with all the goo...

13-Jun-2023
The UK’s effort to alleviate IoT security issues reduces the associated hardware risks. Hardware-...

13-Dec-2023
The White House released a memo by the Office of Management and Budget (OMB) Director Shalanda Yo...

12-Jul-2023
A large corporate bank identified a suspicious transaction within the enterprise. Upon further in...

12-Jul-2023
Zero Trust (ZT) is a security concept that follows the principle of “never trust, always verify.”...

12-Jul-2023
For a country to provide the necessary security for its citizens, it relies on its critical infra...

11-Jul-2023
Let’s consider a simple scenario – you have Lexmark printers connected across several locations i...

10-Jan-2024
Have you ever wondered about the role of human behavior in your organization’s internal cybersecu...

09-Nov-2023
The use case of insider threats is complex and multifaceted. Often dramatized in films and televi...

09-Jan-2023
The NIST Cybersecurity Framework (NIST CSF) is a voluntary framework developed by the National In...

06-Sep-2022
Many network-based cybersecurity tools rely on traffic monitoring in order to provide clients wit...

06-Oct-2023
In an age dominated by digital transformation, organizations must secure themselves against a myr...

06-Jun-2023
You are a security specialist for a large bank – if asked, most would categorize your organizatio...

03-Oct-2023
In the interconnected world of today’s IT/OT/IoT infrastructure, the hardware devices we use, oft...

03-Apr-2023
Sepio named in the 2023 Gartner® Market Guide for Medical Device Security Solutions

02-Mar-2023
Securing networking infrastructure to meet financial institution grade toughness requires protect...

02-Aug-2023
In this article, we address the security risks associated with the Raspberry Pi, whether the inte...
3.png)
01-Jan-2023
Due to the growing number of cyberattacks and their increasing severity, financial regulators are...