

For years, phishing scams would occasionally show up within Dalton State College’s email system.
As a retailer, we have a large number of locations far from the corporate HQ.
Phishing attacks are becoming more and more sophisticated all the time – the problem is identif...
ARPR, the southeast’s largest tech PR agency and one of the fastest growing security of its clie...
As soon as we started digitizing our business, our risk profile increased exponentially.
Headquartered in London, with R&D facilities, manufacturing plants and data centers all over the...
In today’s digital environment it’s incredibly hard to be aware of all the possible incidents w...
Ayrshire College provides further and higher education to students in the Ayrshire region of Scot...
Unified Women’s Healthcare is the largest OB-GYN physician practice management company in the US...
The mobile app is a key benefit from my side. A few times now I’ve received alerts in the evening...
Phishing attacks themselves are not new but using AI and ML has allowed attackers to be more soph...
During the pandemic email became one of the major forms of communication, which increased the ris...
Allegheny Millwork is a leader in the custom millwork industry, providing clients with the highe...
Perimeter 81 is a cybersecurity organization dedicated to helping customers manage and secure th...
Recovery Unplugged is a US-based addiction treatment organization with seven facilities across F...
Bhaktivedanta Hospital and Research Institute is one of the largest hospitals in India, located ...
Before IRONSCALES we needed multiple engineers to hunt down a malicious email, understand what t...
Phishing attacks themselves are not new but using AI and ML has allowed attackers to be more soph...
IRONSCALES...outperforms competing products for the shear breadth of coordinated coverage threat ...
Phishing attacks remain the single biggest cybersecurity threat your company faces today, with b...
A truly effective email security solution should include both This document
Ransomware is a major threat to every business. Every single day, organizations around the world...
Cybercrime will cost enterprises $5.2 trillion within the next
Domain-based Message Authentication, Reporting, and Conformance (DMARC)
As the email phishing threat landscape continues to rapidly evolve, understanding the totality o...
Advanced email phishing attacks remains the most problematic cyber security issue that companies...
Get Mailbox-Level Protection To Prevent And Detect Bec Threats In Progress
What if your email security solution was automatically notified of new email phishing threats the...
Discover the experiences of security experts who secured their Office 365 email environments.
Phishing websites, also known as spoofed websites, are a very common deception tactic that attack...
Legacy email protection technologies like Secure Email Gateways (SEGs) sit in front of your inbox...
Ransomware is a plague on companies of all shapes and sizes around the globe, with no signs of ...
Phishing attacks remain the single biggest cybersecurity threat your company faces today, with ...
How businesses can reduce the time from phishing attack detection to response from hours and da...
Phishing is a type of cybersecurity attack experienced by all organizations. Successful attacks r...
Before Ironscales, lots of phishing emails were reaching the user’s Inbox. This was a big securi...
Cloud Email Security with Advanced Threat Protection. Get continuous protection against phishing...
Ensure your employees are a strong line of defense against the latest methods of attack with Secu...
Award-winning video content to enhance your employee training efforts
Email is a necessity, yet simply clicking a link can expose you or your organization to infectio...
A striking paradox lies at the heart of modern email security. Despite high levels of confidence ...
SRC Cyber Solutions LLP, is part of an 80+ years business house in India, that has recently diver...
Watch NowSRC Ironscales VIP Impersonation Protection
Watch NowSRC Ironscales MS Teams Protection in 60 Seconds
Watch NowSRC Ironscales Integration with Okta
Watch NowSRC Ironscales ATO Protection in 60 Seconds
Watch NowSRC Ironscales ATO Protection in 60 Seconds
Watch NowSRC Ironscales 101 MSI installation
Watch NowPhishing simulation campaigns are vital for businesses to test their employee's security awarenes...
Watch NowNo E-books available.

31-Jan-2024
In the digital age, where email is a cornerstone of communication, particularly in the business s...

31-Jan-2022
International law enforcement collaboration led to the disbandment of several high-profile ransom...

31-Jan-2022
FIN7 is a unique group in the shady world of cybercrime. Infamous for sophisticated stolen credit...
30-Nov-2021
Here at IRONSCALES, we often speak with organizations about their messaging incident response pro...

30-Jun-2022
What Is Smishing? Smishing is a type of social engineering scam that uses mobile texting rather ...

30-Jan-2023
IRONSCALES is an exceptional solution to prevent phishing attacks due to the strength of Themis, ...

29-Nov-2022
What Phishing Threats Are Lurking in Your Inbox? It’s well known that a good security strategy c...

29-Jan-2025
Spam filtering has been around forever, but let’s be honest—traditional methods haven’t exactly k...

28-May-2022
The sensitive nature of information gathered about patients makes healthcare organizations partic...

28-May-2022
If you’re concerned that your security team may be suffering from fatigue, lacking motivation, or...

28-May-2022
For the security-minded, the rise of cryptocurrencies has been both a blessing and a curse. Coins...

28-May-2022
“Yeah, I get it, but I just don't trust users; they always screw everything up,” lamented the Dir...

28-May-2022
“I know I hear you talk about this all the time, but what is ransomware exactly?” my wife asked a...

28-May-2022
A half-century has passed since the first electronic messages were sent via connected ARPANET com...

28-May-2022
Transportation companies provide critical functions in shipping products and carrying people to t...

28-Mar-2023
URL Rewriting, a service used to sandbox and defang malicious URLs by sending users to a portal t...

28-Jul-2023
AI in cybersecurity involves the application of artificial intelligence and machine learning algo...

27-Oct-2022
It may be wrong to admit, but I love a good con. It is the art of deception that fascinates me th...

27-Nov-2024
Email is the lifeline for the modern organization. It’s used to communicate, set meetings, share ...

26-Sep-2023
In my two decades of working in product management and marketing for various cybersecurity techno...

26-Jan-2023
State and local government agencies store, utilize, and send massive amounts of sensitive informa...

26-Aug-2022
3 Ways to Boost Awareness and Prevent Phishing Attacks When it comes to email security, no amoun...

26-Apr-2023
Phishing has been a constant threat in cybersecurity, and as technology evolves, so do the tactic...

25-Oct-2023
Phishing is a social engineering technique that aims to trick the victim into providing sensitive...

25-Jan-2023
As we look ahead to 2023, it's clear that artificial intelligence (AI) will continue to shape the...

25-Jan-2022
FIN7 is a unique group in the shady world of cybercrime. Infamous for sophisticated stolen credit...

25-Feb-2022
5 Email Security and Phishing Predictions for 2022 (Part 2) Being prepared for the latest email ...

25-Aug-2023
Business email compromise (BEC) is one of the most costly and damaging types of email threats, as...

24-Nov-2023
Artificial Intelligence (AI) has become a technology centre point across every industry now a day...

24-Mar-2023
“Large organizations (with 10,000 or more employees) anticipate a 43.3% increase in the threat of...

24-Jul-2023
We're happy to announce the release of Presumed Safe emails. This capability provides privileged ...

24-Jan-2024
If you're a cybersecurity practitioner for an SMB, you know the drill. You're often a one-person ...

24-Feb-2023
While 90% of all cyber breaches originate from phishing emails, traditional anti-phishing solutio...

23-Sep-2022
How to Improve Your Email Security in 24 Hours Cybersecurity Awareness month is right around the...

23-Feb-2022
Disrupting operations at manufacturing plants is a potentially lucrative path for threat actors s...

23-Dec-2021
Ransomware attacks have been on the rise throughout 2021, affecting everyone from large enterpris...

22-Jun-2022
What is Whaling? Whaling is a type of spear phishing in which threat actors directly target c-le...

22-Feb-2024
IP reputation is a measure of the trustworthiness of an IP address based on its past behavior. IP...

21-Nov-2021
Hackers can use their abilities to do good, to do bad and sometimes just to show what they can do...

21-Jun-2023
IRONSCALES, the leading enterprise cloud email security platform protecting more than 10,000 glob...

21-Jul-2022
A SEG By Any Other Name Is Still A SEG The email security market is full of vendors offering a w...

21-Dec-2023
Let's touch on a topic that IT/Security admins can't afford to overlook—phishing simulation testi...

21-Aug-2023
These well-planned attacks are specifically selected, coordinated, and socially engineered to app...

2026-01-31
QR codes are everywhere in schools—and so are the phishing attacks hiding inside them. 15,000+ ma...

2026-01-10
MSPs must shift QBRs from operational reviews to risk-focused discussions, aligning with client-s...
.png)
2026-01-02
ATOs are the new BEC. We're seeing it on our end and other companies have certainly taken notice....

2025-11-07
Discover how to transform Security Awareness Training (SAT) from a compliance checkbox into an op...
.png)
2025-11-03
I've been giving talks lately about the evolution of phishing attacks - tracking them from the Ni...

2025-09-15
Check out our latest resources, expert tips, and tools to maximize your organization's cybersecur...
2025-07-03
Discover what three cybersecurity leaders — SRC, IRONSCALES, and more — are saying about the bigg...
.jpg)
2025-06-12
Cyber threats are evolving, and employee awareness is key to defense. SRC Cyber Solutions offers ...

2025-06-02
Discover how combining email security with DMARC creates a powerful defense against phishing, spo...

20-Sep-2022
The Case Against URL Rewriting For Email Security URL Rewriting, a service used to sandbox and d...

20-Jun-2022
Resource efficiency vs. maximum security – why they don’t have to be at odds At its core, your e...

20-Jan-2022
Netwalker is a notorious name on the ransomware scene with a prolific record of successful attack...

20-Dec-2022
Phishing attacks are surging. As a result, threat actors are quickly evolving their tactics to by...

20-Aug-2021
The State of Ransomware Attacks in the Retail Industry Ransomware attacks pose serious cybersecu...

19-Oct-2022
What aviation can teach you about email security Defense in depth is a common practice in both t...

19-Nov-2018
To Prevent Email Phishing Risks, It’s a Race Against the Clock When it comes to beating a phishi...

19-Jul-2022
Disrupting operations at manufacturing plants is a potentially lucrative path for threat actors s...

18-Oct-2022
The Business Cost of Phishing report reveals organizations with 25 IT and security professionals ...

18-Jan-2022
Ransomware Gangs: Netwalker Netwalker is a notorious name on the ransomware scene with a prolifi...

17-Nov-2022
What Is Your Company’s REAL Click Rate On Phishing Emails? Sometimes I hear the following from s...

17-Nov-2022
How Much Does Phishing Cost Businesses? Cybercriminals have relied on phishing emails as a gatew...

17-Aug-2022
Is It Finally the Time To Let AI Drive Our Cyber Defenses and Security Operations? Cyber securit...

16-Jul-2018
The Evolution of Email Security from Spam Filters to Business Email Compromise Protection Ever s...
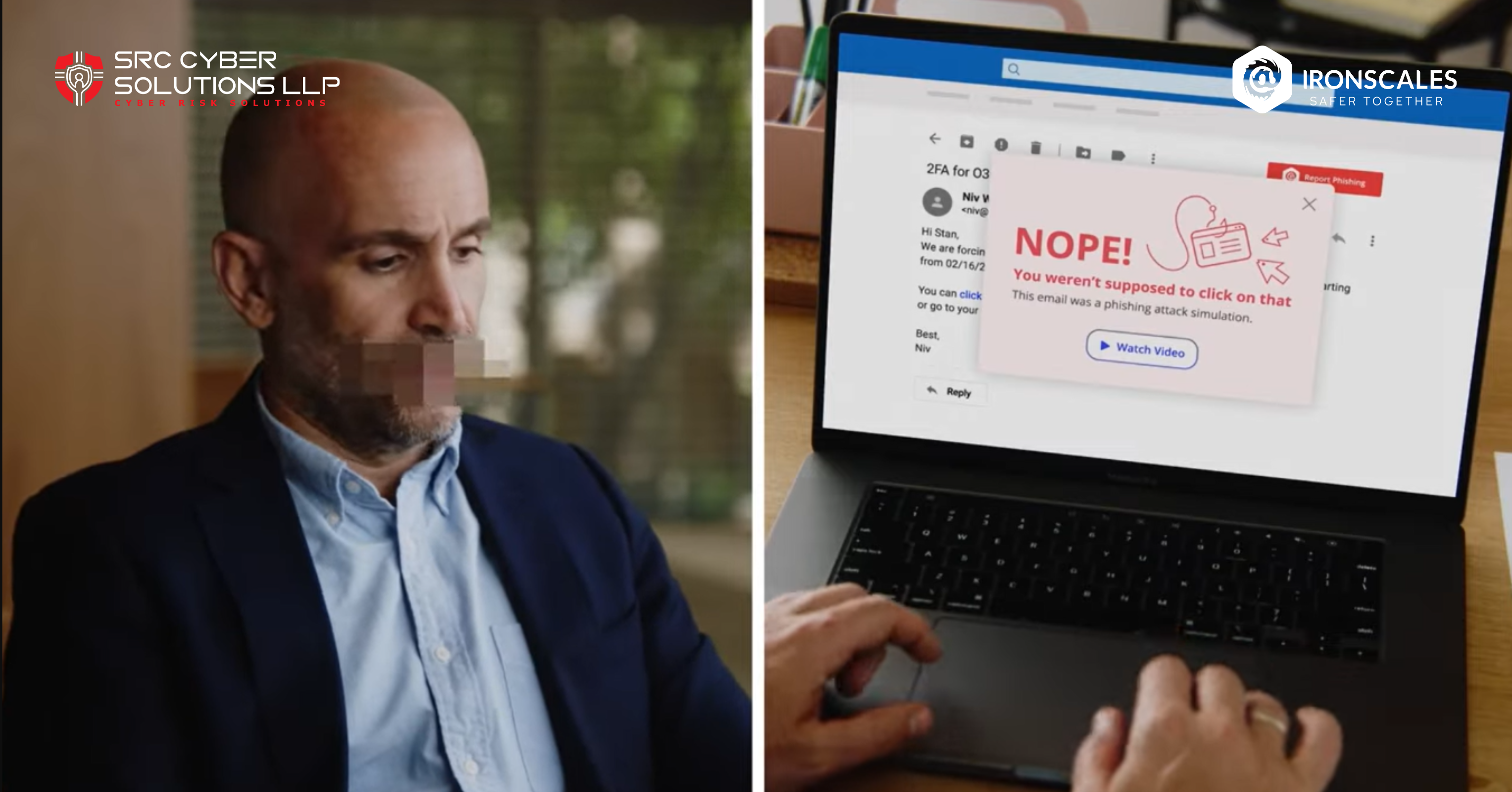
16-Feb-2024
Guess what? While you were reading this sentence, another company just fell victim to a phishing ...

16-Feb-2022
5 Email Security and Phishing Predictions for 2022 (Part 1) In the dynamic world of cybersecurit...

15-Sep-2022
Ransomware Gangs: 0ktapus In 2022, a large-scale phishing campaign successfully compromised IT r...
15-Aug-2022
The Cons of Email Blocklists For organizations dealing with phishing attacks, it may seem like a...

14-Sep-2022
Vendor Spoof Attack Exposes Business Email Credentials A researcher at IRONSCALES recently disco...

14-Jun-2022
EMOTET malware is a banking trojan that was initially spotted in 2014, disappeared for a while, a...

14-Jun-2022
What is Business Email Compromise? Business email compromise (BEC) is a type of targeted phishin...

14-Aug-2023
In the ever-evolving world of cyber threats, threat actors are constantly finding new ways to exp...

13-Dec-2024
Email Security Leader Introduces Advanced Features Designed to Combat AI-Driven Phishing, Strengt...

12-Oct-2022
The Artificial Intelligence (AI) vs. Human Intelligence (HI) debate has been discussed a lot in t...

12-Jul-2022
Crypto Phishing Scam Cryptocurrency is a digital medium of exchange that is not associated with ...

12-Feb-2024
Struggling with email invoice scams can be a nightmare for any business. These devious schemes th...

11-Oct-2022
The 2022 Uber Breach: Social Engineering and the Lapsus$ Gang A cyber-attack on ride-hailing com...

11-Jan-2024
In today's fast-paced digital world, businesses increasingly rely on technology for their day-to-...

11-Aug-2023
Here are the top cybersecurity tools, platforms, capabilities, services, and technologies launche...

11-Aug-2022
Sorry To Burst Your Optimism Every family has its IT guy, ours is Raphael and he is great at it....

10-Oct-2023
It’s no secret that cybercriminals leverage current events and holidays to mask their phishing at...

10-Nov-2022
3 Ways Your SEG is Failing Your Email Security Strategy Secure Email Gateways (SEG)s have been a...

10-Jul-2023
Barrel phishing or “double-barreled phishing” is a form of spear phishing where the attacker send...
10-Jan-2024
The line between personal and professional life is increasingly blurred, especially when it comes...

10-Jan-2023
Phishing simulation campaigns are vital for businesses to test their employee's security awarenes...

10-Jan-2023
The CFO’s role in cybersecurity is often overlooked. Yet, they can be a vital partner with a CISO...

10-Feb-2023
The phishing problem isn’t going away anytime soon. In reality, it’s getting worse as attackers a...

09-Nov-2022
Is Your Organization Vulnerable to Account Takeover? Almost every business or organization is a ...

09-Nov-2021
Ransomware Gangs: Egregor Egregor is a ransomware-as-a-service gang that has so far managed to c...

09-Mar-2023
What is BEC Payroll Diversion? Payroll diversion is a type of business email compromise (BEC) at...

09-Jan-2024
Email security is often a cat-and-mouse game where cybercriminals utilize new phishing technologi...

09-Dec-2024
Microsoft 365’s impersonation and spoofing controls are frustratingly bad. But you’re not alone i...

09-Aug-2022
IRONSCALES Adds Security Awareness Training Many people don’t know that IRONSCALES started as a ...

08-Sep-2022
How Account Takeover (ATO) Attacks Work Account takeover (ATO) attacks involve threat actors gai...

08-Nov-2022
Will Deepfake Emails Lead to Phishing 3.0? For good and bad, AI is now more accessible and used ...

08-Dec-2022
Threat actors constantly tweak and refine their tactics in an attempt to evade detection or becom...

07-Jul-2022
Ransomware Gangs: Black Basta After a cull that saw several high-profile ransomware gangs disban...
07-Aug-2023
Brute force attacks pose a significant threat to information security, as they aim to gain unauth...

07-Aug-2023
In the Email Security dashboard, there are multiple ways to see whether the system has taken an a...

06-Mar-2023
Last month, Gartner published their findings and recommendations from 1,500+ customer interaction...

06-Jun-2023
According to an Osterman Research report, phishing has worsened for most organizations. With the ...

06-Jan-2023
The cybersecurity industry has been talking about collaborative approaches forever. In fact, the ...

06-Apr-2022
It seems like there are two or three posts every day on social media where cyber security compani...

05-May-2023
Phishing simulation campaigns are vital for businesses to test their employee's security awarenes...

05-Mar-2023
To unleash the power of AI, it’s essential to integrate some human input. The technical term is R...

03-Jun-2023
The phishing landscape is morphing rapidly. Cybercriminals are devising various attacks leveragin...
03-Jan-2022
Babuk is a new ransomware gang that emerged in early 2021. The gang’s initial mission statement r...

03-Feb-2024
The difference between safety and a data breach often hinges on a single email. But for IT and se...

03-Aug-2023
In today's digital landscape, the threat of phishing attacks continues to rise, affecting organiz...

03-Aug-2022
How your university can reduce the threat of cyberattacks Eyal Benishti, CEO and Founder, IRONSC...

02-Mar-2023
While Microsoft Defender can provide some protection, relying solely on it as the only layer of d...

02-Mar-2022
Fostering channel partnerships with reputable value-added resellers (VARs) has become an importan...

02-Feb-2023
Propelled by 58% revenue growth, multiple product advancements, and ample analyst recognition in ...

02-Aug-2022
Ransomware Gangs: Cuba While several high-profile ransomware gangs saw a steep rise and an equal...

01-Sep-2022
Ransomware Gangs: Evil Corp Evil Corp is a cybercrime gang notorious for its prolific malware-ba...

01-Jun-2022
The World Cup Ticketing Scam If you're one of the estimated 3 million football/soccer fans looki...

01-Jul-2022
Wave of Phishing Attacks Possible with OpenSea Data Breach OpenSea, the largest non-fungible toke...

01-Jan-2019
The Three Must-Haves of a Truly Automated Email Security Solution Today, everything is automated...
01-Jan-1970
Let’s get straight to the point, email-based attacks present a serious security threat for organi...

01-Feb-2023
ChatGPT is a powerful machine learning-based text generation tool that can generate highly sophis...

01-Feb-2023
Cybersecurity Analyst & Incident Response Expert An intuitive senior-level cybersecurity analyst...